Since 19 november 2022 apt-get update on Debian 8 Jessie gives the follwowing error/warning when running apt-get update:
W: GPG error: http://archive.debian.org jessie Release:
The following signatures were invalid: KEYEXPIRED 1587841717
The contents of my /etc/apt/sources.list:
deb http://archive.debian.org/debian/ jessie main contrib non-free
deb http://deb.freexian.com/extended-lts jessie-lts main contrib non-free
The expired keys:
apt-key list
/etc/apt/trusted.gpg.d/debian-archive-jessie-automatic.gpg
pub 4096R/2B90D010 2014-11-21 [expired: 2022-11-19]
uid Debian Archive Automatic Signing Key (8/jessie) <ftpmaster@debian.org>
/etc/apt/trusted.gpg.d/debian-archive-jessie-security-automatic.gpg
pub 4096R/C857C906 2014-11-21 [expired: 2022-11-19]
uid Debian Security Archive Automatic Signing Key (8/jessie) <ftpmaster@debian.org>
I have the debian-archive-keyring package installed.
I tried to update the keys, using:
gpg --keyserver keyring.debian.org --recv-key 2B90D010
gpg --keyserver keyring.debian.org --recv-key C857C906
But these keys do not seem to be known on keyring.debian.org:
gpg: requesting key 2B90D010 from hkp server keyring.debian.org
gpgkeys: key 2B90D010 can't be retrieved
gpg: no valid OpenPGP data found.
gpg: Total number processed: 0
gpg: requesting key C857C906 from hkp server keyring.debian.org
gpgkeys: key C857C906 can't be retrieved
gpg: no valid OpenPGP data found.
gpg: Total number processed: 0`
So I suppose my questions are:
All keys on the archive.debian.org site are expired.
- Am I trying to update the keys against the correct keyserver (keyring.debian.org)?
- If that is not the issue, then will somebody at Debian fix this (update and publish keys)?
- If no, then is there a way to get rid of the warnings when
apt-get updateandapt-get installare run?
Sep 29, 2016 22:36
· 310 words
· 2 minute read
ubuntu
Обновление программного обеспечения и управление пакетами в Debian-based операционных системах обычно не вызывает вопросов, однако вы можете столкнуться с сообщением KEYEXPIRED. Давайте разберемся, как обновить просроченные ключи!
Симптомы примерно следующие:
apt-get update
Hit http://packages.dotdeb.org jessie InRelease
Ign http://ftp.debian.org jessie InRelease
Hit http://security.debian.org jessie/updates InRelease
Ign http://nginx.org jessie InRelease
Get:1 http://nginx.org jessie Release.gpg [287 B]
Hit http://ftp.debian.org jessie Release.gpg
Get:2 http://nginx.org jessie Release [2,331 B]
Hit http://ftp.debian.org jessie Release
Get:3 http://packages.dotdeb.org jessie/all amd64 Packages [86.5 kB]
Err http://nginx.org jessie Release
Hit http://security.debian.org jessie/updates/main amd64 Packages
Hit http://security.debian.org jessie/updates/main Translation-en
Ign http://packages.dotdeb.org jessie/all Translation-en_US
Ign http://packages.dotdeb.org jessie/all Translation-en
Hit http://ftp.debian.org jessie/main amd64 Packages
Hit http://ftp.debian.org jessie/main Translation-en
Fetched 89.1 kB in 1s (67.2 kB/s)
Reading package lists... Done
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: http://nginx.org jessie Release: The following signatures were invalid: KEYEXPIRED 1471427554
W: Failed to fetch http://nginx.org/packages/mainline/debian/dists/jessie/Release
W: Some index files failed to download. They have been ignored, or old ones used instead.
Как видим, устарел ключ для репозитория nginx — нужно его обновить. Проверить все имеющиеся ключи в системе можно командой:
apt-key list
...
pub 2048R/7BD9BF62 2011-08-19 [expired: 2016-08-17]
uid nginx signing key < signing-key@nginx.com >
...
Вывести только просроченные ключи:
apt-key list | grep expired:
pub 2048R/7BD9BF62 2011-08-19 [expired: 2016-08-17]
Теперь обновим ключ, полученный на предыдущем этапе:
apt-key adv --recv-keys --keyserver keys.gnupg.net 7BD9BF62
Executing: gpg --ignore-time-conflict --no-options --no-default-keyring --homedir /tmp/tmp.Y4AY2GAbZO --no-auto-check-trustdb --trust-model always --keyring /etc/apt/trusted.gpg --primary-keyring /etc/apt/trusted.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-jessie-automatic.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-jessie-security-automatic.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-jessie-stable.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-squeeze-automatic.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-squeeze-stable.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-wheezy-automatic.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-wheezy-stable.gpg --recv-keys --keyserver keys.gnupg.net 7BD9BF62
gpg: requesting key 7BD9BF62 from hkp server keys.gnupg.net
gpg: key 7BD9BF62: "nginx signing key < signing-key@nginx.com >" 6 new signatures
gpg: Total number processed: 1
gpg: new signatures: 6
Теперь можно вернуться к обновлению пакетов в системе — ошибка должна исчезнуть:
apt-get update && apt-get upgrade
tweet
Share
I’ve got the problem, that the «apt-get update» produced a KEYEXPIRED 1587841717 error:
# apt-get update
...
W: GPG error: http://archive.debian.org jessie Release: The following signatures were invalid: KEYEXPIRED 1587841717
Here my sources.list:
# cat /etc/apt/sources.list.d/sources.list
deb http://http.debian.net/debian jessie main
deb http://http.debian.net/debian jessie contrib
deb http://archive.debian.org/debian jessie main
deb http://archive.debian.org/debian jessie contrib
Here the expired keys found by apt-key (it seems that the key 46925553 expired on 2020-04-25):
apt-key list | grep expired -A1
pub 4096R/46925553 2012-04-27 [expired: 2020-04-25]
uid Debian Archive Automatic Signing Key (7.0/wheezy) <ftpmaster@debian.org>
--
pub 4096R/65FFB764 2012-05-08 [expired: 2019-05-07]
uid Wheezy Stable Release Key <debian-release@lists.debian.org>
--
pub 4096R/B98321F9 2010-08-07 [expired: 2017-08-05]
uid Squeeze Stable Release Key <debian-release@lists.debian.org>
--
pub 4096R/473041FA 2010-08-27 [expired: 2018-03-05]
uid Debian Archive Automatic Signing Key (6.0/squeeze) <ftpmaster@debian.org>
--
pub 4096R/65FFB764 2012-05-08 [expired: 2019-05-07]
uid Wheezy Stable Release Key <debian-release@lists.debian.org>
--
pub 4096R/46925553 2012-04-27 [expired: 2020-04-25]
uid Debian Archive Automatic Signing Key (7.0/wheezy) <ftpmaster@debian.org>
Now i tried to renew the keys:
apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys 46925553
apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys 65FFB764
apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys B98321F9
apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys 473041FA
But the keys are not changed:
# apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys 46925553
Executing: gpg --ignore-time-conflict --no-options --no-default-keyring --homedir /tmp/tmp.Ue8AFETZOi --no-auto-check-trustdb --trust-model always --keyring /etc/apt/trusted.gpg --primary-keyring /etc/apt/trusted.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-jessie-automatic.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-jessie-security-automatic.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-jessie-stable.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-stretch-automatic.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-stretch-security-automatic.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-stretch-stable.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-wheezy-automatic.gpg --keyring /etc/apt/trusted.gpg.d/debian-archive-wheezy-stable.gpg --keyring /etc/apt/trusted.gpg.d/debian.gpg --keyring /etc/apt/trusted.gpg.d/php.gpg --keyring /etc/apt/trusted.gpg.d/turnkey.gpg --keyring /etc/apt/trusted.gpg.d/ubuntuzilla.firefox.gpg --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys 46925553
gpg: requesting key 46925553 from hkp server keyserver.ubuntu.com
gpg: key 46925553: "Debian Archive Automatic Signing Key (7.0/wheezy) <ftpmaster@debian.org>" not changed
gpg: Total number processed: 1
gpg: unchanged: 1
A new «apt-get update» get the same error like above.
Can anybody help to solve the problem?
Running an Ubuntu or Debian operating system on your servers comes with a long lifetime. You won’t switch servers and migrate your applications that often.
You’ll maintain your system now and then and update installed packages to keep your system secure.
Recently, while maintaining the software on our server, we ran into the error „The following signatures were invalid: KEYEXPIRED 1544811256“ while running apt-get update.
This error happens when your system installs services from third-party repositories as we do with MongoDB.
Ubuntu/Debian Series Overview
The Problem
You’ll recognize the following output while running apt-get update on your Ubuntu 16.04 system:
$ sudo apt-get update
Ign:11 https://repo.mongodb.org/apt/ubuntu xenial/mongodb-org/3.6 InRelease
Hit:12 https://repos.sonar.digitalocean.com/apt main InRelease
Hit:13 https://repo.mongodb.org/apt/ubuntu xenial/mongodb-org/3.6 Release
Err:17 https://repo.mongodb.org/apt/ubuntu xenial/mongodb-org/3.6 Release.gpg
The following signatures were invalid: KEYEXPIRED 1544811256
Fetched 1930 kB in 3s (601 kB/s)
Reading package lists... Done
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: https://repo.mongodb.org/apt/ubuntu xenial/mongodb-org/3.6 Release: The following signatures were invalid: KEYEXPIRED 1544811256
W: Failed to fetch https://repo.mongodb.org/apt/ubuntu/dists/xenial/mongodb-org/3.6/Release.gpg The following signatures were invalid: KEYEXPIRED 1544811256
W: Some index files failed to download. They have been ignored, or old ones used instead.
The GPG key of the MongoDB repository expired on this server. To fix this issue, you need to rotate the key on your system. Here are the steps to renew an expired key.
Step 1: Find the Expired Key
Find the expired key from apt’s key list. You can run apt-key list to print a list of all installed keys. Use the command below if you want to filter for expired keys:
$ sudo apt-key list | grep -A 1 expired
pub 4096R/91FA4AD5 2016-12-14 [expired: 2018-12-14]
uid MongoDB 3.6 Release Signing Key <packaging@mongodb.com>
This resulting list prints all packages with related key details. The important part is the key 91FA4AD5. Copy that part, because you need it in the second step.
At the time of writing this tutorial, it’s December 18th, 2018 and the key expired four days ago (December 14th, 2018).
Step 2: Renew the Expired Key
Now that you know which key expired, go ahead and renew it. Use the following command and replace the <KEY> placeholder with your key’s value (the one you copied from above):
$ sudo apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys <KEY>
For the expired MongoDB GPG key, the command and output looks like this:
$ sudo apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys 91FA4AD5
Executing: /tmp/tmp.XC8EiRvH3E/gpg.1.sh --keyserver
hkp://keyserver.ubuntu.com:80
--recv-keys
91FA4AD5
gpg: requesting key 91FA4AD5 from hkp server keyserver.ubuntu.com
gpg: key 91FA4AD5: "MongoDB 3.6 Release Signing Key <packaging@mongodb.com>" 1 new signature
gpg: Total number processed: 1
gpg: new signatures: 1
Sweet! Processing the key finished and your system received a new signature. Run the command to find outdated keys again and ensure an empty list.
Step 3: Re-Run Update
Now go ahead and re-run the apt-get update command to update your repositories 👌
$ sudo apt-get update
That’s it. Now you can upgrade your system with the updated packages. Enjoy!
Updating expired keys on Debian and Ubuntu
Software updates and package management is easy with systems based on Debian or Ubuntu. Just apt-get update (or apt update) and run an upgrade. But sometimes you may encounter the following situation: a KEYEXPIRED message.
root# apt-get update && apt-get upgrade
Get:1 http://security.ubuntu.com/ubuntu xenial-security InRelease [94.5 kB]
Hit:2 http://nl.archive.ubuntu.com/ubuntu xenial InRelease
Get:3 http://nl.archive.ubuntu.com/ubuntu xenial-updates InRelease [95.7 kB]
Hit:4 http://nl.archive.ubuntu.com/ubuntu xenial-backports InRelease
Hit:5 https://packages.cisofy.com/community/lynis/deb stable InRelease
Get:6 http://nl.archive.ubuntu.com/ubuntu xenial-updates/main amd64 Packages [373 kB]
Ign:7 http://nginx.org/packages/mainline/ubuntu xenial InRelease
Get:8 http://nginx.org/packages/mainline/ubuntu xenial Release [2,309 B]
Get:9 http://nginx.org/packages/mainline/ubuntu xenial Release.gpg [287 B]
Get:10 http://nl.archive.ubuntu.com/ubuntu xenial-updates/main i386 Packages [368 kB]
Get:11 http://nl.archive.ubuntu.com/ubuntu xenial-updates/universe amd64 Packages [319 kB]
Get:12 http://nl.archive.ubuntu.com/ubuntu xenial-updates/universe i386 Packages [316 kB]
Err:9 http://nginx.org/packages/mainline/ubuntu xenial Release.gpg
The following signatures were invalid: KEYEXPIRED 1471427554
Fetched 1,566 kB in 0s (2,003 kB/s)
Reading package lists… Done
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: http://nginx.org/packages/mainline/ubuntu xenial Release: The following signatures were invalid: KEYEXPIRED 1471427554
W: Failed to fetch http://nginx.org/packages/mainline/ubuntu/dists/xenial/Release.gpg The following signatures were invalid: KEYEXPIRED 1471427554
W: Some index files failed to download. They have been ignored, or old ones used instead.
Reading package lists… Done
Building dependency tree
Reading state information… Done
Calculating upgrade… Done
The following packages will be upgraded:
apparmor libapparmor-perl libapparmor1 python3-distupgrade python3-software-properties software-properties-common ubuntu-release-upgrader-core
7 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
Need to get 0 B/672 kB of archives.
After this operation, 5,120 B of additional disk space will be used.
Do you want to continue? [Y/n] y
The KEYEXPIRED shows that validation failed on the related repository signature. This is a good thing, to warn us that we should be checking the repository. With an expired key, the solution is simple: we need to download an updated key. Apparently it is for the nginx repository.
Step 1: Run apt-key
Using the apt-key utility we can display all the known keys.
apt-key list
In our case, we see the nginx key is expired a few days ago:
pub 2048R/7BD9BF62 2011-08-19 [expired: 2016-08-17]
uid nginx signing key <signing-key@nginx.com>
Two items are highlighted in this example. The first one is the short version of the key. The second one is showing that the key is expired (including the date). This key was valid for almost 5 years.
To quickly find the expired keys, search for “expired:”:
apt-key list | grep “expired:”
Step 2: Update the key
We can now use the key gathered in step 1 to update it:
apt-key adv --keyserver keys.gnupg.net --recv-keys [KEY]
The output might look like this:
The key is renewed, after choosing the right one (otherwise no change is made)
On purpose we selected an incorrect key, which was also related to nginx:
/etc/apt/trusted.gpg.d/nginx-development.gpg
——————————————–
pub 1024R/C300EE8C 2010-07-21
uid Launchpad Stable
As you can see in the output above, nothing happens when you select the wrong key.
Step 3: Update
After renewing the expired key you can run apt update again and install any available upgrades.
apt update && apt upgrade
Happy upgrading!
One more thing…
Keep learning
So you are interested in Linux security? Join the Linux Security Expert training program, a practical and lab-based training ground. For those who want to become (or stay) a Linux security expert.
See training package

Run automated security scans and increase your defenses. Lynis is an open source security tool to perform in-depth audits. It helps with system hardening, vulnerability discovery, and compliance.
Download
Возможно исправить ?
W: GPG error: http://archive.debian.org jessie Release: The following signatures were invalid: KEYEXPIRED 1587841717
Можно просто игнорировать , тогда пакеты для Jessie будут устанавливаться без ошибок ?
Так как ключ относится сразу к разным версиям Debian , а эта ошибка из-за ключа от wheezy
Цифровая подпись нужна для подтверждения целостности пакета, соответственно если ключ не валидный, цифровая подпись не действительна. Соответственно целостность не гарантируется.
dpkg -i проверял всё так же осталось
Удалите ключ от Wheezy и всё… Конечно если вы им не пользуетесь.
apt-key del 46925553
apt-get update
W: GPG error: http://archive.debian.org jessie Release: The following signatures couldn’t be verified because the public key is not available: NO_PUBKEY 8B48AD6246925553
Тогда поставьте пакет от Debian Stretch.
В нём уже Wheezy нет, а только Jessie, Stretch и Buster: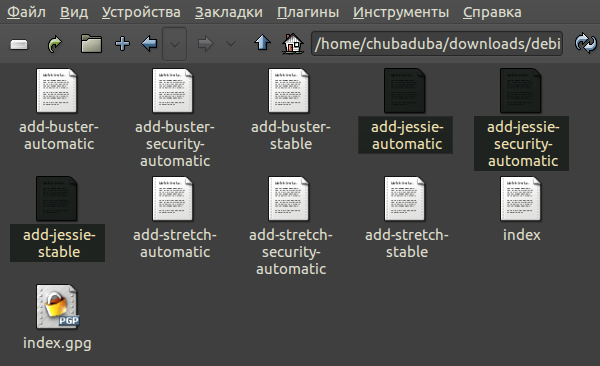
dpkg -i debian-archive-keyring_2017.5+deb9u1_all.deb
apt-key update
apt-get update
W: GPG error: http://archive.debian.org jessie Release: The following signatures couldn’t be verified because the public key is not available: NO_PUBKEY 8B48AD6246925553
$ cat /etc/apt/sources.list
Отправил сообщение в ЛС
Без результатов
Кто знает как оставить только ключ jessie
и удалить ключ wheezy
чтобы не было сообщения
закончился срок действия ключа wheezy
Пожалуйста напишите
sudo apt-key list
Примерный вывод
pub 1024R/B455BEF0 2010-07-29
uid Launchpad clicompanion-nightlies
Соответственно удалить
sudo apt-key del B455BEF0
One highly unlikely, but occasionally possible, cause for this error is if having added the same key twice with different expiry dates. You would likely know having done so for this answer to be relevant to you.
This can happen, as it did for me, when hosting your own repository with your own keys. If you, when the key is about to expire, simply extend its lifetime rather than change it, and if you installed the original key using preseeding but the updated key using a deb package, then the old key will be in /etc/apt/trusted.gpg, while the new one ends up as a separate file under /etc/apt/trusted.gpg.d/. The old key will shadow the new one, which will be completely ignored by apt-key. Remove the old key by running gpg --keyring /etc/apt/trusted.gpg --delete-keys <keyid>, and your new key will become detected.
This is a bit of a non-standard corner configuration, but I hope my answer can save some confusion in case anyone else encounters this issue due to the same reason as I did.
None of these worked for me:
$ sudo apt-key adv --keyserver hkp://pgp.mit.edu:80 --recv-keys 5072E1F5
or
$ sudo apt-key adv --keyserver pgp.mit.edu --recv-keys 5072E1F5
or
$ sudo apt-key adv --keyserver pgp.mit.edu --recv-keys A4A9406876FCBD3C456770C88C718D3B5072E1F5
The sources for those are:
https://bugs.mysql.com/bug.php?id=85029 and https://bugs.mysql.com/bug.php?id=94378
I performed one suspect operation in desperation (saying ‘y’ instead of ‘N’ below) which I think wasn’t required at all:
$ sudo apt-get install mysql-apt-config
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following packages will be upgraded:
mysql-apt-config
1 upgraded, 0 newly installed, 0 to remove and 294 not upgraded.
Need to get 35.6 kB of archives.
After this operation, 0 B of additional disk space will be used.
WARNING: The following packages cannot be authenticated!
mysql-apt-config
Install these packages without verification? [y/N] y
Get:1 http://repo.mysql.com/apt/ubuntu/ trusty/mysql-apt-config mysql-apt-config all 0.8.13-1 [35.6 kB]
Fetched 35.6 kB in 0s (229 kB/s)
Preconfiguring packages ...
dpkg-deb: error: archive '/var/cache/apt/archives/mysql-apt-config_0.8.13-1_all.deb' has premature member 'control.tar.xz' before 'contro
l.tar.gz', giving up
dpkg: error processing archive /var/cache/apt/archives/mysql-apt-config_0.8.13-1_all.deb (--unpack):
subprocess dpkg-deb --control returned error exit status 2
Errors were encountered while processing:
/var/cache/apt/archives/mysql-apt-config_0.8.13-1_all.deb
E: Sub-process /usr/bin/dpkg returned an error code (1)
And followed it with:
$ sudo apt-get update
which did not help.
I still got the same error.
Finally, the following worked:
$ sudo apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv-keys 5072E1F5
I’m speculating (blindly) that maybe pgp.mit.edu has changed their structure or maybe «MySQL Release Engineering» (run apt-key list) has moved their keys to the ubuntu key server or some such thing (I have no idea of how keys are maintained).
This comment on the duplicate thread says the same thing.
Hope this saves someone some time and effort.

