All about secure apt
Debian uses strong cryptography to validate downloaded packages. This is commonly called «secure apt» (or «apt-secure») and was implemented in Apt version 0.6 in 2003, which Debian migrated to in 2005. Since the documentation (here and here) is fairly slim on how this all works from an administrator’s point of view, this document will try to explain in detail how secure apt works and how to use it.
This article discusses things at a relatively high level. For details on the format of the files Debian repositories please refer to the DebianRepository/Format page. For detailed information on commands please refer to the man pages of the tools.
Contents
- All about secure apt
- Basic concepts
- Secure apt groundwork: checksums
- Signed Release files
- How apt uses Release.gpg
- How to tell apt what to trust
- How to find and add a key
- How to tell if the key is safe
- Debian archive key expiry
- How to manually check for package’s integrity
- Other problems
- Setting up a secure apt repository
- Failed updates and missing keys
- History
- Comments and questions
Basic concepts
Here are a few basic concepts that you’ll need to understand for the rest of this document.
A secure hash function (a type of checksum) is a method of taking a file and boiling it down to a reasonably short number that will uniquely identify the content of the file, even if people are deliberately trying to create a pair of different files with the same checksum or create a new file that matches a previous checksum. APT was originally designed around MD5 but people have since managed to construct collisions and so support for newer hash functions has been added.
Public key cryptography is based on pairs of keys, a public key and a private key. The public key is given out to the world; the private key must be kept a secret. Anyone possessing the public key can encrypt a message so that it can only be read by someone possessing the private key. It’s also possible to use a private key to sign a file, not encrypt it. If a private key is used to sign a file, then anyone who has the public key can check that the file was signed by that key. Anyone who doesn’t have the private key can’t forge such a signature.
These keys are quite long numbers (at least 1024 bits, i.e. 256 or more hex digits and preferably a lot more), and to make them easier to work with they have a key id, which is a shorter, 8 or 16 digit number that can be used to refer to them. However care should be taken with key IDs, especially the short 8 character ID as it is possible to generate collisions.
apt currently uses gpg as the OpenPGP implementation to verify signatures.
apt-key is a program that is used to manage a keyring of OpenPGP keys for secure apt. The keyring is kept in the file /etc/apt/trusted.gpg (not to be confused with the related but not very interesting /etc/apt/trustdb.gpg). apt-key can be used to show the keys in the keyring, and to add or remove a key. In more recent Debian GNU/Linux versions (Wheezy, for example), the keyrings are stored in specific files all located in the /etc/apt/trusted.gpg.d directory. For example, that directory could contain the following files: debian-archive-squeeze-automatic.gpg or debian-archive-wheezy-automatic.gpg. Incidentally, both files are provided by the debian-archive-keyring package.
Secure apt groundwork: checksums
A Debian archive contains a Release file, which is updated each time any of the packages in the archive change. Among other things, the Release file contains some checksums of other files in the archive. An excerpt of an example Release file:
MD5Sum: 6b05b392f792ba5a436d590c129de21f 3453 Packages 1356479a23edda7a69f24eb8d6f4a14b 1131 Packages.gz 2a5167881adc9ad1a8864f281b1eb959 1715 Sources 88de3533bf6e054d1799f8e49b6aed8b 658 Sources.gz
Now if we look inside a Packages file, we’ll find more checksums, one for each package listed in it. For example:
Package: uqm Priority: optional ... Filename: unstable/uqm_0.4.0-1_amd64.deb Size: 580558 MD5sum: 864ec6157c1eea88acfef44d0f34d219
These two checksums allow apt to verify that it has downloaded a correct copy of the Packages file, with a checksum that matches the one in the Release file. And when it downloads an individual package, it can also check its checksum against the content of the Packages file. If apt fails at either of these steps, it will abort.
None of this is new in secure apt, but it does provide the foundation. Notice that so far there is one file that apt doesn’t have a way to check: The Release file. Secure apt is all about making apt verify the Release file before it does anything else with it, and plugging this hole, so that there is a chain of verification from the package that you are going to install all the way back to the provider of the package.
Signed Release files
To plug the hole, secure apt adds an OpenPGP signature for the Release file. This is put in a file named Release.gpg that’s shipped alongside the Release file. It looks something like this, although only an OpenPGP implementation actually looks at its contents normally:
-----BEGIN PGP SIGNATURE----- Version: GnuPG v1.4.1 (GNU/Linux) iD8DBQBCqKO1nukh8wJbxY8RAsfHAJ9hu8oGNRAl2MSmP5+z2RZb6FJ8kACfWvEx UBGPVc7jbHHsg78EhMBlV/U= =x6og -----END PGP SIGNATURE-----
(Technically speaking, this is an ASCII-armored detached OpenPGP signature.)
How apt uses Release.gpg
Secure apt always downloads Release.gpg files when it’s downloading Release files, and if it cannot download the Release.gpg, or if the signature is bad, it will complain, and will make note that the Packages files that the Release file points to, and all the packages listed therein, are from an untrusted source. Here’s how it looks during an apt-get update:
W: GPG error: https://deb.debian.org testing Release: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 010908312D230C5F
Note that the second half of the long number is the key id of the key that apt doesn’t know about, in this case that’s 2D230C5F.
If you ignore that warning and try to install a package later, apt will warn again:
WARNING: The following packages cannot be authenticated! libglib-perl libgtk2-perl Install these packages without verification [y/N]?
If you say Y here you have no way to know if the file you’re getting is the package you’re supposed to install, or if it’s something else entirely that a black hat has arranged for you, containing a nasty surprise.
Note that you can disable these checks by running apt with —allow-unauthenticated.
It’s also worth noting that newer versions of the Debian installer use the same signed Release file mechanism during their debootstrap of the Debian base system, before apt is available, and that the installer even uses this system to verify pieces of itself that it downloads from the net. Also, Debian does not currently sign the Release files on its CDs; apt can be configured to always trust packages from CDs so this is not a large problem.
How to tell apt what to trust
So the security of the whole system depends on there being a Release.gpg file, which signs a Release file, and of apt checking that signature using gpg. To check the signature, it has to know the public key of the person who signed the file. These keys are kept in apt’s own keyring (/etc/apt/trusted.gpg), and managing the keys is where secure apt comes in.
By default, Debian systems come preconfigured with the Debian archive key in the keyring.
user@host:~> sudo apt-key list
/etc/apt/trusted.gpg.d/debian-archive-bullseye-stable.gpg
---------------------------------------------------------
pub rsa4096 2021-02-13 [SC] [expires: 2029-02-11]
A428 5295 FC7B 1A81 6000 62A9 605C 66F0 0D6C 9793
uid [ unknown] Debian Stable Release Key (11/bullseye) <debian-release@lists.debian.org>
Here A428 5295 FC7B 1A81 6000 62A9 605C 66F0 0D6C 9793 is the key fingerprint, and notice that this key is only valid for a limited period. Debian occasionally rotates these keys as a last line of defense against some sort of security breach breaking a key.
That will make apt trust the official Debian archive, but if you add some other apt repository to /etc/apt/sources.list, you’ll also have to give apt its key if you want apt to trust it. Once you have the key and have verified it, it’s a simple matter of «apt-key add file» to add it. Getting the key and verifying it are the trickier part.
How to find and add a key
The debian-archive-keyring package is used to distribute keys to apt. Upgrades to this package can add (or remove) OpenPGP keys for the main Debian archive.
For other archives, there is not yet a standard location where you can find the key for a given apt repository. There’s a rough standard of putting the key up on the web page for the repository or as a file in the repository itself, but no real standard, so you might have to hunt for it.
The current and the retired Debian archive «signing» keys are available from https://ftp-master.debian.org/keys.html.
The OpenPGP ecosystem has a standard way to distribute keys, using a keyserver that OpenPGP implementation can use to download a key from and add it to a keyring. For example with Sequoia-PGP:
user@host:~> sq keyserver get --binary --output debian-archive-bullseye-stable.pgp 'A428 5295 FC7B 1A81 6000 62A9 605C 66F0 0D6C 9793'
Or with GnuPG:
user@host:~> gpg --keyserver hkps://keyserver.ubuntu.com --recv-keys 'A428 5295 FC7B 1A81 6000 62A9 605C 66F0 0D6C 9793' gpg: key 605C66F00D6C9793: public key "Debian Stable Release Key (11/bullseye) <debian-release@lists.debian.org>" imported gpg: Total number processed: 1 gpg: imported: 1 user@host:~> gpg --output debian-archive-bullseye-stable.pgp --export 'A428 5295 FC7B 1A81 6000 62A9 605C 66F0 0D6C 9793'
To install the keyring simply copy it to the apt trusted.gpg.d directory:
user@host:~> sudo cp -i debian-archive-bullseye-stable.pgp /etc/apt/trusted.gpg.d/
How to tell if the key is safe
By adding a key to apt’s keyring, you’re telling apt to trust everything signed by the key, and this lets you know for sure that apt won’t install anything not signed by the person who possesses the private key. But if you’re sufficiently paranoid, you can see that this just pushes things up a level, now instead of having to worry if a package, or a Release file is valid, you can worry about whether you’ve actually gotten the right key. Is the information on https://ftp-master.debian.org/keys.html mentioned above correct or is this all some clever trap?
It’s good to be paranoid in security, but verifying things from here is harder. OpenPGP has the concept of a chain of trust, which can start at someone you’re sure of, who signs someone’s key, who signs some other key, etc., until you get to the archive key. If you’re sufficiently paranoid you’ll want to check that your archive key is signed by a key that you can trust, with a trust chain that goes back to someone you know personally. If you want to do this, visit a Debian conference or perhaps a local LUG for a key signing.
(Note: Not all apt repository keys are signed at all by another key. Maybe the person setting up the repository doesn’t have another key, or maybe they don’t feel comfortable signing such a role key with their main key.)
If you can’t afford this level of paranoia, do whatever feels appropriate to you when adding a new apt source and a new key. Maybe you’ll want to mail the person providing the key and verify it, or maybe you’re willing to take your chances with downloading it and assuming you got the real thing. The important thing is that by reducing the problem to what archive keys to trust, secure apt lets you be as careful and secure as it suits you to be.
Here’s a blog post with a procedure to verify the key’s integrity. See also Securing Debian, Ch7.
Debian archive key expiry
Since secure apt was introduced, the keys used to sign the main Debian archive have changed a couple of times. Since secure apt is young, we don’t have a great deal of experience with changing the key and there are still rough spots.
In January 2006, a new key for 2006 was made and the Release file began to be signed by it, but to try to avoid breaking systems that had the old 2005 key, the Release file was signed by that as well. The intent was that apt would accept one signature or the other depending on the key it had, but apt turned out to be buggy and refused to trust the file unless it had both keys and was able to check both signatures. This was fixed in apt version 0.6.43.1. There was also confusion about how the key was distributed to users who already had systems using secure apt; initially it was uploaded to the web site with no announcement and no real way to verify it and users were forced to download it by hand. This was fixed by the introduction of the debian-archive-keyring package, which manages apt keyring updates.
In late 2006, a new key was created that will be used to sign the archive for the lifetime of the Debian 4.0 release (until 2009-07-01). The archive began to be signed by this new key in addition to the yearly signing key for 2006. That was a bit confusing, because the key began to be used before it was announced and before debian-archive-keyring was updated to include it! Apt’s warning message in this situation is slightly opaque to end users. There’s obviously still room for improvement in how we roll out new keys. This new key does answer the question of how users of the 4.0 (etch) release will be able to validate their software for the lifetime of that release. This new key is also being used to sign other versions of Debian (like unstable).
On February 7th 2007, the 2006 key expired. Currently the only known breakage of this is that it broke rc1 of the etch installer, since the installer images only know about the 2006 key. Daily builds of the installer have the 2007 key and continue to work.
Most recently, a new Etch stable release key has been added. This key is an offline key that will be used to sign releases of Etch (including point releases).
How to manually check for package’s integrity
There are sometimes you want to manually check that a package hasn’t been tampered since the time it was uploaded to the archive and the time you downloaded it. The apt system will take care of this procedure automatically, but in this section we will describe how to perform these safety tests manually.
First, we’re assuming you have downloaded the Release information from a trusted source (official Debian servers and mirrors). You’ll need to check the Release file as the first step, for that you’ll use the signature Release.gpg file, as in the following example.
Note: You will have to import the public key for the archive, if it isn’t in your keyring; and use your current distribution instead of «sid».
cd /var/lib/apt/lists
gpgv --keyring /etc/apt/trusted.gpg deb.debian.org_debian_dists_sid_Release.gpg
deb.debian.org_debian_dists_sid_Release
After that you check the md5sums of the Packages file for each of the components. For example:
# Print the md5sum of the Packages file which is listed in the Release file.
sed -n "s,main/binary-amd64/Packages$,,p" deb.debian.org_debian_dists_sid_Release
# Print the md5sum of the Packages file itself.
md5sum deb.debian.org_debian_dists_sid_main_binary-amd64_Packages
Finally, we check the MD5 or SHA checksum of the package itself.
apt-cache show <package_name> | sed -n "s/MD5sum: //p" # Grab the checksum from the APT cache. md5sum <binary_package_name>.deb # Compare it against the binary package's checksum.
This section is far from complete, but we expect is a good introductory material for digging into the Debian packages’ trust chain.
TODO: Add signature verification: dscverify quick introduction.
Other problems
- One not so obvious gotcha is that if your clock is very far off, secure apt will not work. If it’s set to a date in the past, such as 1999, apt will fail with an unhelpful message such as this:
W: GPG error: https://archive.progeny.com sid Release: Unknown error executing gpg
Although apt-key list will make the problem plain:
gpg: key 2D230C5F was created 192324901 seconds in the future (time warp or clock problem) gpg: key 2D230C5F was created 192324901 seconds in the future (time warp or clock problem) pub 1024D/2D230C5F 2006-01-03 uid Debian Archive Automatic Signing Key (2006) <ftpmaster@debian.org>
If it’s set to a date too far in the future, apt will treat the keys as expired.
- Another problem you may encounter if using testing or unstable is that if you have not run apt-get update lately and apt-get install a package, apt might complain that it cannot be authenticated (why does it do this?). apt-get update will fix this.
- If apt gives a warning like this:
W: There are no public key available for the following key IDs: A70DAF536070D3A1
- This means that the archive has begun to be signed by a new key, which your system does not know about. In this example, the new key is a dedicated key that will be used to sign the release of Debian 4.0. Since the archive was still signed by another key that apt knows about, this is just a warning, and once the system is fed the new key (by upgrading the debian-archive-keyring package), the warning will go away.
- If you have the debsig-verify package installed, you might run into errors like this one:
dpkg: error processing /var/cache/apt/archives/anjuta-common_1.2.4a-2_all.deb (--unpack): Verification on package /var/cache/apt/archives/anjuta-common_1.2.4a-2_all.deb failed! Authenticating /var/cache/apt/archives/anjuta-common_1.2.4a-2_all.deb ... debsig: Origin Signature check failed. This deb might not be signed.
This actually has nothing to do with secure apt. debsig-verify checks for signatures embedded inside individual Debian packages. Since such signatures are not widely used (we use secure apt instead), it doesn’t work very well to install this, and removing the debsig-verify package will fix the problem.
- If apt-get update outputs this
W: GPG error: http://non-us.debian.org stable/non-US Release: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY F1D53D8C4F368D5D W: You may want to run apt-get update to correct these problems
remove non-us from /etc/apt/sources.
Setting up a secure apt repository
From man apt-secure
If you want to provide archive signatures in an archive under your maintenance you have to:
- Create a toplevel Release file. if it does not exist already. You can do this by running apt-ftparchive release (provided inftp apt-utils).
- Sign it. You can do this by running gpg -abs -o Release.gpg Release.
- Publish the key fingerprint, that way your users will know what key they need to import in order to authenticate the files in the archive.
Whenever the contents of the archive changes (new packages are added or removed) the archive maintainer has to follow the first two steps previously outlined.
Failed updates and missing keys
Don’t be surprised if you attempt to apt-get upgrade and things do not work as expected. Additionally, trying to resolve the missing key with procedures on this page will fail too. If you encounter the issues, please file a bug report.
Below is a typical set of failures you will encounter using Debian Hurd as an example. Many ports fail the same way.
$ sudo apt-get update Hit https://snapshot.debian.org sid InRelease Get:1 https://ftp.debian-ports.org unreleased InRelease [32.8 kB] Get:2 https://snapshot.debian.org sid/main Sources/DiffIndex [7876 B] Ign https://ftp.debian-ports.org unreleased InRelease Get:3 https://snapshot.debian.org sid/main hurd-i386 Packages/DiffIndex [7876 B] Ign https://ftp.debian-ports.org unreleased/main Sources/DiffIndex Get:4 https://snapshot.debian.org sid/main Translation-en/DiffIndex [7876 B] Ign https://ftp.debian-ports.org unreleased/main hurd-i386 Packages/DiffIndex Err https://ftp.debian-ports.org unreleased/main Sources Err https://ftp.debian-ports.org unreleased/main hurd-i386 Packages Err https://ftp.debian-ports.org unreleased/main Sources Err https://ftp.debian-ports.org unreleased/main hurd-i386 Packages Err https://ftp.debian-ports.org unreleased/main Sources Err https://ftp.debian-ports.org unreleased/main hurd-i386 Packages Hit https://ftp.debian-ports.org unreleased/main Sources Hit https://ftp.debian-ports.org unreleased/main hurd-i386 Packages Ign https://ftp.debian-ports.org unreleased/main Translation-en Fetched 56.4 kB in 5s (10.4 kB/s) Reading package lists... W: GPG error: https://ftp.debian-ports.org unreleased InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY B4C86482705A2CE1 $ sudo apt-get install debian-ports-archive-keyring Reading package lists... Done Building dependency tree Reading state information... Done debian-ports-archive-keyring is already the newest version. 0 upgraded, 0 newly installed, 0 to remove and 8 not upgraded. $ gpg --keyserver hkps://keyserver.ubuntu.com --recv-keys B4C86482705A2CE1 gpg: WARNING: using insecure memory! gpg: please see http://www.gnupg.org/documentation/faqs.html for more information gpg: requesting key 705A2CE1 from hkp server keyserver.ubuntu.com gpg: keyserver timed out gpg: keyserver receive failed: keyserver error $ sudo apt-key update gpg: key B98321F9: "Squeeze Stable Release Key <debian-release@lists.debian.org>" not changed gpg: key 473041FA: "Debian Archive Automatic Signing Key (6.0/squeeze) <ftpmaster@debian.org>" not changed gpg: key 65FFB764: "Wheezy Stable Release Key <debian-release@lists.debian.org>" not changed gpg: key 46925553: "Debian Archive Automatic Signing Key (7.0/wheezy) <ftpmaster@debian.org>" not changed gpg: key 518E17E1: "Jessie Stable Release Key <debian-release@lists.debian.org>" not changed gpg: key 2B90D010: "Debian Archive Automatic Signing Key (8/jessie) <ftpmaster@debian.org>" not changed gpg: key C857C906: "Debian Security Archive Automatic Signing Key (8/jessie) <ftpmaster@debian.org>" not changed gpg: Total number processed: 7 gpg: unchanged: 7
History
Conectiva implemented something similar in their fork of APT. Debian Developers Colin Walters and Isaac Jones implemented APT Secure for Debian in 2003. Around Christmas 2003, Matt Zimmerman(?) integrated this patch into APT 0.6. In February 2005, Debian started migrating to apt-secure.
(Add any here.)
Debian isn’t Ubuntu and won’t have sudo installed by default. It might be worth changing the usage of sudo, and making the examples use the root account explicitly — SteveKemp
Given the failure modes I’ve seen from gpg —recv-keys, suggesting that a user run it as root doesn’t seem wise to me. But I’ve never actually audited it either.. Despite sudo not being installed by default (in sarge), I think that most of the audience of this page are familiar with it, or can skip over it. — JoeyHess
Does it make any sense to pre-install debian-server-keyring on every debian system? At least the user should be asked if s/he trusts this key. Until now (2006-01-07) the Debian Archive Automatic Signing Key is not in the strong set of keys. Thus is it not possible to test via pathfinders if there is a trust path from my key to the Debian Archive Automatic Signing Key. (See http://pgp.cs.uu.nl/ or http://www.lysator.liu.se/~jc/wotsap/search.html)
Yes, the debian-archive-keyring package will be our key upgrade path for all Debian systems, so it should be installed on all of them, and I assume will be in standard. — JoeyHess
Can we somehow integrate this idea into this page? I think it’s important we also move in this direction. — madduck
I tried making a local repository using apt-move, serving machines running testing and stable. I could not use the same repository for both stable and testing due to incopatibilities between apt v5 and v6. You might highlight this when you get around to writing the bit about crating a repository. I could get v6 working for testing but not for sarge. —?MartinHodges
What does it mean for md5sum to be broken? Since it’s a checksum, I thought the only way it can be broken is that it fail to compute the proper checksum. I have a feeling some other meaning is intended. —?RossBoylan
**it is broken as people were able to actually create a fake certificate that could sign anything and was trusted, they did this by finding a collision, they created a certificate that had the same md5 sum as the certificate they were issued, and where thereby able to give themselves right other than they were granted.—Scientes
***apt has supported sha256 checksums since version 0.7.7, so these will be used in lenny and future releases. —JoeyHess
The idea is that generating a checksum from a file is easy, but recreating a file from a checksum (or making another file generate the same checksum) is very hard (ideally, it would be impossible). «md5sum is being broken» means that that «very hard» path becomes quite possible. In other words, it is becoming (or maybe even has become) feasible to create a «rogue» Debian package that still generates the same checksum as the original true package. —JohnZaitseff
I’d say «theoretically possible in certian cases which may or may not include the Debian Packages files», not «quite possible» —JoeyHess
Does Secure APT cover the possibility that the archive machine itself is broken into? What is there to stop someone «inserting» a rogue version of a Debian package and simply regenerating the Packages and Release/Release.gpg files? I strongly suspect this has been considered, but this document does not mention it. Perhaps a link to appropriate documentation, if such exists? —JohnZaitseff
If someone has root access to your machine they already have everything, they do not need to break apt. Detecting if your machine has been broken into is another topic and something extremely difficult, although there are certainly some things debian could do better. —Scientes
Yes, if this happens we can revoke the archive key, and introduce a new key for the new install of ftp-master and rollback of the archive to its last known good state that we’d have to do after such an incident. —JoeyHess
It might be worth linking to https://www.debian.org/doc/manuals/securing-debian-howto/ch7.en.html#s-check-non-debian-releases as it explains briefly how to create the Release and Release.gpg files for repositories. —?JohnLamb
I had a problem where apt gave the dreaded «WARNING: The following packages cannot be authenticated» message despite having debian-archive-keyring installed and having run «apt-get update». It turned out that my sources list contained deb https://security.debian.org/ stable updates/main instead of deb https://security.debian.org/ stable/updates main Apt found the packages file and could find all the debs, but it was not locating the Releases and Releases.gpg files. —AlexKing
Would you add an explanation of why apt-get, apt-key, etc. might run into the GnuPG «resource limit» and how to fix it? This seems to result in the «NO_PUBKEY» warnings even if the respective keys are in the trustdb trusted.gpg. E.g.:
$ sudo apt-key update gpg: keyblock resource `/etc/apt/trusted.gpg.d//webupd8team-java.gpg': resource limit gpg: keyblock resource `/etc/apt/trusted.gpg.d//webupd8team-y-ppa-manager.gpg': resource limit gpg: key 437D05B5: "Ubuntu Archive Automatic Signing Key <ftpmaster@ubuntu.com>" not changed gpg: key FBB75451: "Ubuntu CD Image Automatic Signing Key <cdimage@ubuntu.com>" not changed gpg: key C0B21F32: "Ubuntu Archive Automatic Signing Key (2012) <ftpmaster@ubuntu.com>" not changed gpg: key EFE21092: "Ubuntu CD Image Automatic Signing Key (2012) <cdimage@ubuntu.com>" not changed gpg: Total number processed: 4 gpg: unchanged: 4
—AslamKarachiwala
Note: apt-key is in the process of being deprecated, at least for the managing of keys. Discussion in Debian bug 851774 .
CategoryPermalink | CategoryPackageManagement
When performing apt-get update, I get the following error:
root@ADS3-Debian6:/home/aluno# apt-get update
Atingido http://sft.if.usp.br squeeze Release.gpg
Ign http://sft.if.usp.br/debian/ squeeze/contrib Translation-en
Ign http://sft.if.usp.br/debian/ squeeze/contrib Translation-pt
Ign http://sft.if.usp.br/debian/ squeeze/contrib Translation-pt_BR
(…)
Obter:10 http://security.debian.org squeeze/updates/non-free i386 Packages [14 B]
Baixados 612 kB em 4s (125 kB/s)
Lendo listas de pacotes... Pronto
There is no public key available for the following key IDs: 8B48AD6246925553
asked May 14, 2013 at 17:37
1
The other answers will work, or not, depending on whether or not the key ‘8B48AD6246925553’ is present in the packages they indicate.
If you need a key, you have to get that key, and where to find it, it’s in a key server (very probably any key server will do):
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 8B48AD6246925553
answered May 26, 2015 at 19:10
mariotomomariotomo
2,6101 gold badge14 silver badges11 bronze badges
7
I recommend:
$ sudo apt-get install debian-archive-keyring
$ sudo apt-key update
This is better than other approaches because it does not install debian-keyring, which is big and 99% of the time unnecessary.
GAD3R
60.9k30 gold badges126 silver badges189 bronze badges
answered Jun 12, 2015 at 14:54
5
The error There is no public key available for the following key IDs indicates a serious security issue: an operating-system package cannot be checked for integrity with its public key, because its public key is missing.
If the message were:
There is no public key available for the following key IDs: 1397BC53640DB551
You can use this command to find out which repository uses the key:
for n in `ls /var/lib/apt/lists/*gpg`; do echo "$n" ; gpg --list-packets "$n" | grep 1397BC53640DB551; done
Which in this example is the Google’s repository for Chrome:
/var/lib/apt/lists/dl.google.com_linux_chrome_deb_dists_stable_Release.gpg
If you trust Google, its government, etc., you should find out where the key is and add it with:
wget -q -O - https://dl.google.com/linux/linux_signing_key.pub | apt-key add -
answered Apr 28, 2016 at 10:42
Ivan OgaiIvan Ogai
4164 silver badges4 bronze badges
3
I faced the same problem in Linux Mint (Kernel Version 3.13.0-24) and I was able to solve it using the commands :
gpg --recv-keys <the-reported-key>
gpg --export <the-reported-key> | apt-key add -
Points to be noted:
1) The commands were executed in order
2) The commands were exectued as root user
Courtesy this answer.
answered Jun 29, 2016 at 9:16
My answer is a slight upgrade (IMHO, YMMV) on @mariotomo (who I upvoted) in the following bash scriptlet
- also uses
gpg - parameterizes more
- (also uses a different keyserver, though in this case I suspect it makes little difference)
You can also comment-out the eval line for a «dry-run»: the scriptlet will then only show you what it intends to do, without actually doing it. Just be sure to change the value of NO_PUBKEY every time you use this (you can also change KEYSERVER as desired):
NO_PUBKEY='1397BC53640DB551' # CHANGE TO THE VALUE CITED IN YOUR ERROR MESSAGE!
KEYSERVER='keys.gnupg.net'
NO_PUBKEY_LEN="${#NO_PUBKEY}"
echo "NO_PUBKEY_LEN='${NO_PUBKEY_LEN}'" # for sanity or debugging
# note following works because bash arrays have 0-based indices
NO_PUBKEY_2ND_HALF_START=$(( NO_PUBKEY_LEN/2 ))
echo "NO_PUBKEY_2ND_HALF_START='${NO_PUBKEY_2ND_HALF_START}'" # ditto
NO_PUBKEY_2ND_HALF="${NO_PUBKEY:${NO_PUBKEY_2ND_HALF_START}}"
echo "NO_PUBKEY_2ND_HALF='${NO_PUBKEY_2ND_HALF}'" # ditto
for CMD in
'date'
"gpg --keyserver ${KEYSERVER} --recv-keys ${NO_PUBKEY_2ND_HALF}"
'date'
"gpg -a --export ${NO_PUBKEY_2ND_HALF} | sudo apt-key add -"
; do
echo -e "${CMD}"
eval "${CMD}"
done
answered Apr 29, 2016 at 0:36
TomRocheTomRoche
1,2453 gold badges15 silver badges29 bronze badges
Run killall -q gpg-agent if the other solutions do not work. It may work.
I was getting a similar error for a PPA repository on Ubuntu 18.04 and after trying various solutions on the internet for the last month, I just stumbled on the gpg-agent and killed it. Then the PPA repositries started to update on doing sudo apt-get update. I know it may compromise security, but sometimes you need a package from a PPA, and GPG just doesn’t let you. Later, you start the gpg-agent again, and things go back to normal.
Edward
2,2343 gold badges15 silver badges25 bronze badges
answered Jun 11, 2019 at 6:07
As an alternative:
$ sudo apt-get install debian-keyring debian-archive-keyring
$ sudo apt-key update
slm♦
356k112 gold badges753 silver badges860 bronze badges
answered Dec 6, 2014 at 2:17
1
I just ran into this issue while trying to update a desktop box with a horrible case of laziness-induced installation cobwebs, and fixed it by using my web browser to save the latest available version of the debian-archive-keyring package from https://packages.debian.org/sid/debian-archive-keyring into /tmp, then hand-installing it with dpkg -i /tmp/debian-archive-keyring*.deb.
This procedure is very simple, not subject to tampering via MITM attacks, and the download and installation steps can be done on separate machines if the target machine’s cobwebs are bad enough to require that.
answered May 5, 2020 at 8:39
flabdabletflabdablet
2742 silver badges5 bronze badges
This worked for me:
Quick remedy:
sudo rm -f /etc/apt/trusted.gpg
(Source)
answered Jul 20, 2017 at 21:31

You might see a missing public GPG key error («NO_PUBKEY») on Debian, Ubuntu or Linux Mint when running apt update / apt-get update. This can happen when you add a repository, and you forget to add its public key, or maybe there was a temporary key server error when trying to import the GPG key.
When running an apt update / apt-get update, or trying to refresh the software sources using some GUI tool, apt will complain about not being able to download all repository indexes, showing errors like this:
W: An error occurred during the signature verification. The repository is not updated and the previous index files will be used. GPG error: http://ppa.launchpad.net/linuxuprising/apps/ubuntu bionic InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY EA8CACC073C3DB2A
W: Failed to fetch http://ppa.launchpad.net/linuxuprising/apps/ubuntu/dists/bionic/InRelease The following signatures couldn't be verified because the public key is not available: NO_PUBKEY EA8CACC073C3DB2A
W: Some index files failed to download. They have been ignored, or old ones used instead.This is just an example. This error can occur not only with Launchpad PPA repositories, but any repository, like those provided by Google, Vivaldi or Node.js, etc.
The error message says that the repository is not updated, and the previous index files will be used. That means you won’t receive updates from that repository, so you should import the public GPG key to fix this issue.
This is how to easily fix the The following signatures couldn't be verified because the public key is not available: NO_PUBKEY ... error. It should work on Debian, Ubuntu, Linux Mint, Pop!_OS, elementary OS, and any other Linux distribution based on Debian or Ubuntu.
Solution 1: Quick NO_PUBKEY fix for a single repository / key.
If you’re only missing one public GPG repository key, you can run this command on your Ubuntu / Linux Mint / Pop!_OS / Debian system to fix it:
sudo apt-key adv --keyserver hkp://pool.sks-keyservers.net:80 --recv-keys THE_MISSING_KEY_HEREYou’ll have to replace THE_MISSING_KEY_HERE with the missing GPG key. The key is shown in the apt update / apt-get update log, after NO_PUBKEY. For example, in the error message I posted above, the missing GPG key that must be used in this command is EA8CACC073C3DB2A.
Also see: How To Fix «Could not get lock /var/lib/dpkg/lock — open (11 Resource temporarily unavailable)» Errors
Solution 2: Batch import all missing GPG keys.
When you’re missing multiple public OpenPGP keys you can use a this one-liner to import all of them in one go:
sudo apt update 2>&1 1>/dev/null | sed -ne 's/.*NO_PUBKEY //p' | while read key; do if ! [[ ${keys[*]} =~ "$key" ]]; then sudo apt-key adv --keyserver hkp://pool.sks-keyservers.net:80 --recv-keys "$key"; keys+=("$key"); fi; done
There’s no need to change any part of the command, just run it as is. This also works for fixing a single missing GPG key, but it’s a bit redundant. Nonetheless, it works with any number of missing GPG keys.
The command runs sudo apt update to update your software sources and detect missing GPG keys, and it imports each missing key using hkp://pool.sks-keyservers.net:80 as its server. This server is synchronized with many other servers continuously, so it should have updated keys. You could use some other server if you wish.
The command also uses an array to store missing GPG keys for which we’ve already imported the key. Without that, the key import command would run twice for each missing key.
You might also be interested in: How To Make A PGP Key On Linux Using A GUI (And Publish It)
I added some extra repositories with the Software Sources program. But when I reload the package database, I get an error like the following:
W: GPG error: http://ppa.launchpad.net trusty InRelease: The following signatures couldn’t be verified because the public key is not available: NO_PUBKEY 8BAF9A6F
I know I can fix it using apt-key in a terminal, according to the official Ubuntu documentation. But I would have liked to do it graphically. Is there a way to do this without using a terminal?
Wilf
29.1k16 gold badges103 silver badges162 bronze badges
asked Nov 13, 2010 at 20:27
8
Execute the following commands in terminal
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys <PUBKEY>
where <PUBKEY> is your missing public key for repository, e.g. 8BAF9A6F.
Then update
sudo apt-get update
ALTERNATE METHOD:
sudo gpg --keyserver pgpkeys.mit.edu --recv-key <PUBKEY>
sudo gpg -a --export <PUBKEY> | sudo apt-key add -
sudo apt-get update
Note that when you import a key like this using apt-key you are telling the system that you trust the key you’re importing to sign software your system will be using. Do not do this unless you’re sure the key is really the key of the package distributor.
cjs
2851 silver badge11 bronze badges
answered Nov 28, 2010 at 18:49
karthick87karthick87
79.3k59 gold badges192 silver badges232 bronze badges
18
By far the simplest way to handle this now is with Y-PPA-Manager (which now integrates the launchpad-getkeys script with a graphical interface).
-
To install it, first add the webupd8 repository for this program:
sudo add-apt-repository ppa:webupd8team/y-ppa-manager -
Update your software list and install Y-PPA-Manager:
sudo apt-get update sudo apt-get install y-ppa-manager -
Run y-ppa-manager (i.e. type
y-ppa-managerthen press enter key). -
When the main y-ppa-manager window appears, click on «Advanced.»
-
From the list of advanced tasks, select «Try to import all missing GPG keys» and click OK.
You’re done! As the warning dialog says when you start the operation, it may take quite a while (about 2 minutes for me) depending on how many PPA’s you have and the speed of your connection.
answered Dec 4, 2013 at 15:52
monotaskermonotasker
3,6251 gold badge17 silver badges14 bronze badges
18
It happens when you don’t have a suitable public key for a repository.
To solve this problem use this command:
gpg --keyserver hkp://keyserver.ubuntu.com:80 --recv 9BDB3D89CE49EC21
which retrieves the key from ubuntu key server. And then this:
gpg --export --armor 9BDB3D89CE49EC21 | sudo apt-key add -
which adds the key to apt trusted keys.
The solution can be found here & here & here.
Kevin Bowen
19.2k55 gold badges75 silver badges81 bronze badges
answered Mar 27, 2011 at 22:31
PedramPedram
5,4933 gold badges29 silver badges37 bronze badges
6
You need to get and import the key.
To get the key from a PPA, visit the PPA’s Launchpad page. On every PPA page at Launchpad you will find this link (2), after clicking on ‘Technical details about this PPA’ (1):
Follow it and click on the key ID link (3):
Save the page, this is your key file.
Now it’s time to import it:
Applications > Software Center,Edit > Software sources...,- Enter your password,
- Go to the
Authenticationtab and click onImport Key File..., finally - Select the saved key file and click on
OK.
xiota
4,6295 gold badges24 silver badges52 bronze badges
answered Nov 13, 2010 at 21:04
htorquehtorque
63.2k39 gold badges194 silver badges218 bronze badges
5
apt can only handle 40 keys in /etc/apt/trusted.gpg.d . 41 keys and you will get the GPG error «no public key found» even if you go through all the steps to add the missing key(s).
Check to see if there are any unused keys in this file from ppa(s) you no longer use. If all are in use, consider removing some ppa(s) along with the corresponding keyfiles in /etc/apt/trusted.gpg.d
Furthermore, using
sudo apt-key adv
Is considered a security risk and is not recommended as you are «undermining the whole security concept as this is not a secure way of recieving keys for various reasons (like: hkp is a plaintext protocol, short and even long keyids can be forged, …)«. http://ubuntuforums.org/showthread.php?t=2195579
I believe the correct way to add missing keys (for example 1ABC2D34EF56GH78) is
gpg --keyserver hkp://keyserver.ubuntu.com:80 --recv 1ABC2D34EF56GH78
gpg --export --armor 1ABC2D34EF56GH78 | sudo apt-key add -
answered Aug 7, 2014 at 22:33
mchidmchid
40.6k6 gold badges92 silver badges141 bronze badges
10
There is a tiny script packaged in the WebUpd8 PPA which I’ll link as a single .deb download so you don’t have to add the whole PPA — which automatically imports all missing GPG keys.
Download and install Launchpad-getkeys (ignore the ~natty in its version, it works with all Ubuntu versions from Karmic all the way to Oneiric). Once installed, open a terminal and type:
sudo launchpad-getkeys
If you’re behind a proxy, things are a bit more complicated so see this for more info
answered Jun 5, 2011 at 20:15
Alin AndreiAlin Andrei
7,3284 gold badges41 silver badges55 bronze badges
2
I faced the same issue while installing Heroku. The link below solved my problem —
http://naveenubuntu.blogspot.in/2011/08/fixing-gpg-keys-in-ubuntu.html
After fixing the NO_PUBKEY issue, the below issue remained
W: GPG error: xhttp://toolbelt.heroku.com ./ Release: The following signatures were invalid: BADSIG C927EBE00F1B0520 Heroku Release Engineering <release@heroku.com>
To fix it I executed the following commands in terminal:
sudo -i
apt-get clean
cd /var/lib/apt
mv lists lists.old
mkdir -p lists/partial
apt-get clean
apt-get update
Source — Link to solve it
answered Jan 30, 2013 at 17:12
dennyacdennyac
2175 silver badges7 bronze badges
1
Make sure you have apt-transport-https installed:
dpkg -s apt-transport-https > /dev/null || bash -c "sudo apt-get update;
sudo apt-get install apt-transport-https -y"
Add repository:
curl https://repo.skype.com/data/SKYPE-GPG-KEY | sudo apt-key add -
echo "deb [arch=amd64] https://repo.skype.com/deb stable main" | sudo tee /etc/apt/sources.list.d/skype-stable.list
Install Skype for Linux:
sudo apt-get update
sudo apt-get install skypeforlinux -y
Source: https://community.skype.com/t5/Linux/Skype-for-Linux-Beta-signatures-couldn-t-be-verified-because-the/td-p/4645756
answered May 27, 2017 at 20:00
More generally, the following method should work for every repository. First of all search, with eventual help of a search engine, for a text on the program provider’s website looking like the following:
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: GnuPG v1.4.1 (GNU/Linux)
[...]
-----END PGP PUBLIC KEY BLOCK-----
Such a text is for example displayed on http://deb.opera.com. Copy the passage, paste it in an empty file that you create on your desktop. This results in the key file.
Then continue with the importation of the key:
- Applications > Sofware Center
- Edit > Sofware sources…, enter password
- Authentication tab, click on ‘Import Key File…’
- Select the saved key file and click on ‘Ok’.
You may now remove the previously created key file.
answered Nov 13, 2010 at 21:43
AgmenorAgmenor
15.5k18 gold badges65 silver badges103 bronze badges
0
This error can also occur when the apt list file by the PPA points to a local keyring, like
deb [signed-by=/usr/share/keyrings/SOMETHING.gpg] https://download.something.org/something something/
And while that file may exist on your system (possibly downloaded with a prior command), it may be unreadable due to missing permissions. I just fixed this kind of error by running
chmod 644 /usr/share/keyrings/*
after having fetched the keyring file. The underlying issue was the usage of sudo when I already was root user. Really weird as all of this is root anyway and there was no access permission failure message anywhere… but that fixed it
answered Jun 12, 2020 at 12:28
phil294phil294
5397 silver badges16 bronze badges
1
Good! I finaly found the way!
I’ve tested all method’s to fix GPG error NO_PUBKEY and nothing working for me.
I’ve deleted the entire contents of the folder /etc/apt/trusted.gpg.d
cd /etc/apt/trusted.gpg.d
sudo rm -R *
sudo apt-get update
And I use the Y-PPA-Manager method because I’m too lazy to create all pubkey’s manually (too many): http://www.unixmen.com/fix-w-gpg-error-no_pubkey-ubuntu/
run sudo apt-get update again and finaly all work great now! Tanks!
Based Source : post #17 on https://bugs.launchpad.net/ubuntu/+source/apt/+bug/1263540
answered Apr 8, 2015 at 13:36
4
I had the same problem with DynDNS’s Updater client.
Turns out it was just expired keys.
Reinstalling the software (downloading a new .deb from the website, then using Software Centre to reinstall) fixed the problem.
Error message for reference:
W: GPG error: http://cdn.dyn.com stable/ Release: The following signatures were invalid: KEYEXPIRED 141943.......
kos
35k13 gold badges98 silver badges149 bronze badges
answered Jan 8, 2015 at 16:53
CrankyCranky
4245 silver badges11 bronze badges
2021 August. This is what worked for me.
cd /etc/apt/trusted.gpg.d
sudo rm -R *
sudo apt-get update
The last line will raise errors of missing keys.
What you’d then have to do is manually install each of the keys listed in the errors
for example if the error is saying that your missing PUB_KEY is 9BDB3D89CE49EC21,
You can manually add the Key with the command sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 9BDB3D89CE49EC21
Re-run sudo apt-get update
Repeat the process for the new key raised in the error
Say if the new key was 3BDB3D89CE49EC24,
Just Manually add the Key with the command sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 3BDB3D89CE49EC24
Re-run sudo apt-get update and repeat the process until all the errors are gone.
Then go back to the package site you were trying to install and repeat the installation process.
For my case, the error was coming while I tried installing Sublime Text
Doing the above and returning to the Sublime installation guide here solved the issues.
Don’t forget to upvote if this works for you. And it must do
answered Aug 29, 2021 at 6:20
NMukamaNMukama
2961 silver badge13 bronze badges
-
Lightvader
- Posts: 4
- Joined: 2017-10-21 11:40
Can’t apt update, unavailable public key[fixed][solved]
#1
Post
by Lightvader » 2017-10-21 11:58
I can’t update my packages, because the public key is not available.
The problem must have arisen somewhere between last week and today, because I could do this a week ago.
The only things that might have caused this were adding 2 PPAs that i’ve since then removed(by unchecking and deleting the entries with software-properties-gtk).
I tried running
And it gives the following output:
Code: Select all
Ign:1 http://deb.debian.org/debian stretch InRelease
Ign:2 http://deb.debian.org/debian stretch/updates InRelease
Get:3 http://deb.debian.org/debian stretch-updates InRelease [91.0 kB]
Err:3 http://deb.debian.org/debian stretch-updates InRelease
The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 8B48AD6246925553 NO_PUBKEY 7638D0442B90D010
Get:5 http://deb.debian.org/debian stretch Release [118 kB]
Get:4 http://security.debian.org stretch/updates InRelease [62.9 kB]
Err:6 http://deb.debian.org/debian stretch/updates Release
404 Not Found [IP: 151.101.4.204 80]
Err:4 http://security.debian.org stretch/updates InRelease
The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 9D6D8F6BC857C906 NO_PUBKEY 8B48AD6246925553
Get:7 http://deb.debian.org/debian stretch Release.gpg [2479 B]
Ign:7 http://deb.debian.org/debian stretch Release.gpg
Reading package lists... Done
W: GPG error: http://deb.debian.org/debian stretch-updates InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 8B48AD6246925553 NO_PUBKEY 7638D0442B90D010
E: The repository 'http://deb.debian.org/debian stretch-updates InRelease' is not signed.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
E: The repository 'http://deb.debian.org/debian stretch/updates Release' does not have a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: GPG error: http://security.debian.org stretch/updates InRelease: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 9D6D8F6BC857C906 NO_PUBKEY 8B48AD6246925553
E: The repository 'http://security.debian.org stretch/updates InRelease' is not signed.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
W: GPG error: http://deb.debian.org/debian stretch Release: The following signatures couldn't be verified because the public key is not available: NO_PUBKEY 8B48AD6246925553 NO_PUBKEY 7638D0442B90D010 NO_PUBKEY EF0F382A1A7B6500
E: The repository 'http://deb.debian.org/debian stretch Release' is not signed.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
But running
shows that i do have the keys
Code: Select all
[sudo] password for lv:
/etc/apt/trusted.gpg.d/debian-archive-jessie-automatic.gpg
----------------------------------------------------------
pub rsa4096 2014-11-21 [SC] [expires: 2022-11-19]
126C 0D24 BD8A 2942 CC7D F8AC 7638 D044 2B90 D010
uid [ unknown] Debian Archive Automatic Signing Key (8/jessie) <ftpmaster@debian.org>
/etc/apt/trusted.gpg.d/debian-archive-jessie-security-automatic.gpg
-------------------------------------------------------------------
pub rsa4096 2014-11-21 [SC] [expires: 2022-11-19]
D211 6914 1CEC D440 F2EB 8DDA 9D6D 8F6B C857 C906
uid [ unknown] Debian Security Archive Automatic Signing Key (8/jessie) <ftpmaster@debian.org>
/etc/apt/trusted.gpg.d/debian-archive-jessie-stable.gpg
-------------------------------------------------------
pub rsa4096 2013-08-17 [SC] [expires: 2021-08-15]
75DD C3C4 A499 F1A1 8CB5 F3C8 CBF8 D6FD 518E 17E1
uid [ unknown] Jessie Stable Release Key <debian-release@lists.debian.org>
/etc/apt/trusted.gpg.d/debian-archive-stretch-automatic.gpg
-----------------------------------------------------------
pub rsa4096 2017-05-22 [SC] [expires: 2025-05-20]
E1CF 20DD FFE4 B89E 8026 58F1 E0B1 1894 F66A EC98
uid [ unknown] Debian Archive Automatic Signing Key (9/stretch) <ftpmaster@debian.org>
sub rsa4096 2017-05-22 [S] [expires: 2025-05-20]
/etc/apt/trusted.gpg.d/debian-archive-stretch-security-automatic.gpg
--------------------------------------------------------------------
pub rsa4096 2017-05-22 [SC] [expires: 2025-05-20]
6ED6 F5CB 5FA6 FB2F 460A E88E EDA0 D238 8AE2 2BA9
uid [ unknown] Debian Security Archive Automatic Signing Key (9/stretch) <ftpmaster@debian.org>
sub rsa4096 2017-05-22 [S] [expires: 2025-05-20]
/etc/apt/trusted.gpg.d/debian-archive-stretch-stable.gpg
--------------------------------------------------------
pub rsa4096 2017-05-20 [SC] [expires: 2025-05-18]
067E 3C45 6BAE 240A CEE8 8F6F EF0F 382A 1A7B 6500
uid [ unknown] Debian Stable Release Key (9/stretch) <debian-release@lists.debian.org>
/etc/apt/trusted.gpg.d/debian-archive-wheezy-automatic.gpg
----------------------------------------------------------
pub rsa4096 2012-04-27 [SC] [expires: 2020-04-25]
A1BD 8E9D 78F7 FE5C 3E65 D8AF 8B48 AD62 4692 5553
uid [ unknown] Debian Archive Automatic Signing Key (7.0/wheezy) <ftpmaster@debian.org>
/etc/apt/trusted.gpg.d/debian-archive-wheezy-stable.gpg
-------------------------------------------------------
pub rsa4096 2012-05-08 [SC] [expires: 2019-05-07]
ED6D 6527 1AAC F0FF 15D1 2303 6FB2 A1C2 65FF B764
uid [ unknown] Wheezy Stable Release Key <debian-release@lists.debian.org>
This is the output of
Code: Select all
cat /etc/apt/sources.list && ls /etc/apt/sources.list.d/for anyone interested
Code: Select all
deb http://deb.debian.org/debian/ stretch main contrib non-free
deb-src http://deb.debian.org/debian/ stretch main contrib non-free
deb http://deb.debian.org/debian/ stretch/updates main contrib non-free
deb-src http://deb.debian.org/debian/ stretch/updates main contrib non-free
deb http://security.debian.org/ stretch/updates contrib main non-free
deb http://deb.debian.org/debian/ stretch-updates contrib main non-free
alessandro-strada-ubuntu-ppa-artful.list skype-stable.list
I have tried the following to resolve this:
- Installing the debian-keyring and debian-archive-keyring
Code: Select all
sudo apt-get install debian-keyring debian-archive-keyringThe installation of this went without errors, i rebooted, but tryiny to update still had the same problem.
- installing the keys from https://ftp-master.debian.org/keys.html
withCode: Select all
wget -O - https://link/to/key.asc | apt-key add -The following variations
Code: Select all
wget -O - https://ftp-master.debian.org/keys/archive-key-8.asc | apt-key add - sudo wget -O - https://ftp-master.debian.org/keys/archive-key-8.asc | apt-key add - sudo -i wget -O - https://ftp-master.debian.org/keys/archive-key-8.asc | apt-key add -all gave this output
Code: Select all
--2017-10-21 09:08:09-- https://ftp-master.debian.org/keys/archive-key-8.asc Resolving ftp-master.debian.org (ftp-master.debian.org)... E: This command can only be used by root. 138.16.160.17 Connecting to ftp-master.debian.org (ftp-master.debian.org)|138.16.160.17|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 7012 (6.8K) [text/plain] Saving to: 'STDOUT' - 0%[ ] 0 --.-KB/s in 0.03s Cannot write to '-' (Broken pipe).and
Code: Select all
sudo su wget -O - https://ftp-master.debian.org/keys/archive-key-8.asc | apt-key add -gave this
Code: Select all
--2017-10-21 09:12:10-- https://ftp-master.debian.org/keys/archive-key-8.asc Resolving ftp-master.debian.org (ftp-master.debian.org)... 138.16.160.17 Connecting to ftp-master.debian.org (ftp-master.debian.org)|138.16.160.17|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 7012 (6.8K) [text/plain] Saving to: 'STDOUT' - 100%[=====================================================================================================>] 6.85K --.-KB/s in 0.03s 2017-10-21 09:12:11 (269 KB/s) - written to stdout [7012/7012] gpg: WARNING: nothing exported gpg: no valid OpenPGP data found. gpg: Total number processed: 0
What can I do to resolve this?
Last edited by Lightvader on 2017-10-23 09:57, edited 1 time in total.
-
Lightvader
- Posts: 4
- Joined: 2017-10-21 11:40
Re: Can’t apt update, unavailable public key
#3
Post
by Lightvader » 2017-10-21 13:15
Thanks for replying.
Head_on_a_Stick wrote:Can we see the output of:
that would be
Code: Select all
[sudo] password for lv:
debian-keyring:
Installed: 2017.05.28
Candidate: 2017.05.28
Version table:
*** 2017.05.28 500
500 http://deb.debian.org/debian stretch/main amd64 Packages
100 /var/lib/dpkg/status
Head_on_a_Stick wrote:
Have you tried adding the key directly, without the pipe (download the .asc file and place in the working directory beforehand):
Just tried that.
Doesn’t work.
Code: Select all
sudo apt-key add archive-key-9-security.ascand the other keys all give me
Code: Select all
gpg: WARNING: nothing exported
gpg: no valid OpenPGP data found.
gpg: Total number processed: 0
-
Lightvader
- Posts: 4
- Joined: 2017-10-21 11:40
Re: Can’t apt update, unavailable public key
#5
Post
by Lightvader » 2017-10-21 14:46
Thanks,
but that didn’t work. Or, I’m pointing it at the wrong thing.
I tried
Code: Select all
gpg --keyserver keyring.debian.org --recv-keys 0x7638D0442B90D010
gpg --keyserver keyring.debian.org --recv-keys 7638D0442B90D010
gpg --keyserver keyring.debian.org --recv-keys 2B90D010
and they all give me
Code: Select all
gpg: no valid OpenPGP data found.
gpg: Total number processed: 0this also doesn’t work.
Code: Select all
lv@dbian-laptop:~$ gpg --keyserver ftp-master.debian.org --recv-keys 2B90D010
gpg: keyserver receive failed: No keyserver availableWhat keyserver should i point it to?
Also, on the debian keyring page ( https://wiki.debian.org/DebianKeyring ), i found
another method to download the keyrings
Code: Select all
rsync -az --progress keyring.debian.org::keyrings/keyrings/ .
this downloaded some files, namely
debian-keyring.gpg
debian-maintainers.gpg
debian-role-keys.gpg
emeritus-keyring.gpg
extra-keys.pgp
debian-nonupload.gpg
i imported them all with
and tried exporting them and then adding them to apt-keys
Code: Select all
gpg --export --armor keyhash|sudo apt-key add -
with the following keyhashes
46925553
2B90D010
C857C906
F66AEC98
8AE22BA9
That also didn’t work.
Code: Select all
gpg: WARNING: nothing exported
gpg: no valid OpenPGP data found.
for all of them.
Когда вы пытаетесь установить программу из сторонних репозиториев разработчика программы или из PPA вы можете столкнуться с ошибкой gpg недоступен открытый ключ. Это не значит, что программа платная и вам надо приобрести к ней ключ. Дело в том, что для защиты репозиториев от подмены используется подписывание пакетов с помощью GPG ключей.
Для того чтобы пакетный менеджер мог проверить подпись пакета, который вы пытаетесь установить необходимо чтобы у вас в системе был GPG ключ этого репозитория. Для официальных репозиториев ключи поставляются автоматически, а вот для сторонних надо их вручную добавить. Давайте рассмотрим пути решения этой проблемы.
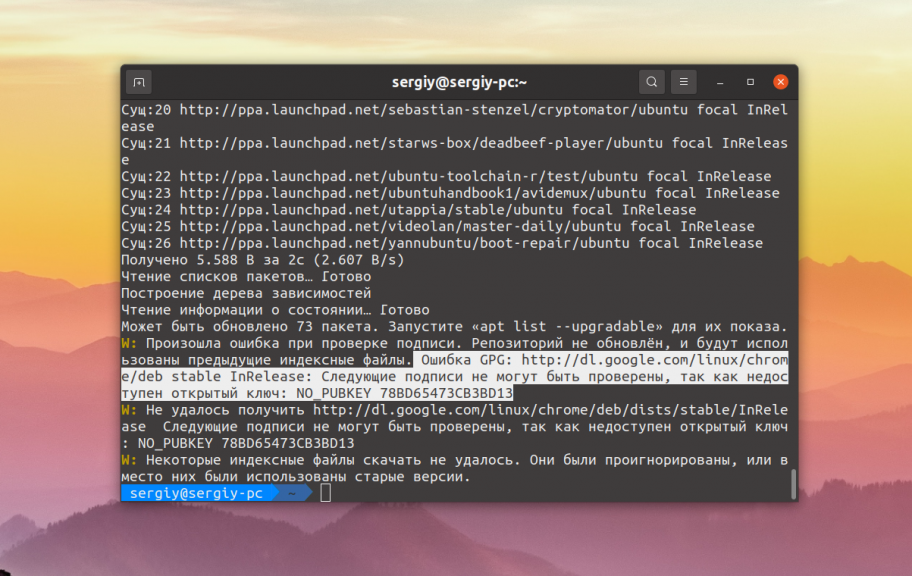
Как вы можете видеть на снимке, программа сообщает какой именно репозиторий вызвал проблему и какого ключа не хватает:
Самый простой и правильный способ решить эту проблему — добавить ключ в систему. Обычно, там где вы нашли информацию о том как добавить репозиторий есть и информация как добавить его ключ. К тому же в выводе информации об ошибке пакетный менеджер сообщает какой ключ он ожидает увидеть. Вы можете попытаться искать такой ключ в Google или на серверах ключей Ubuntu.
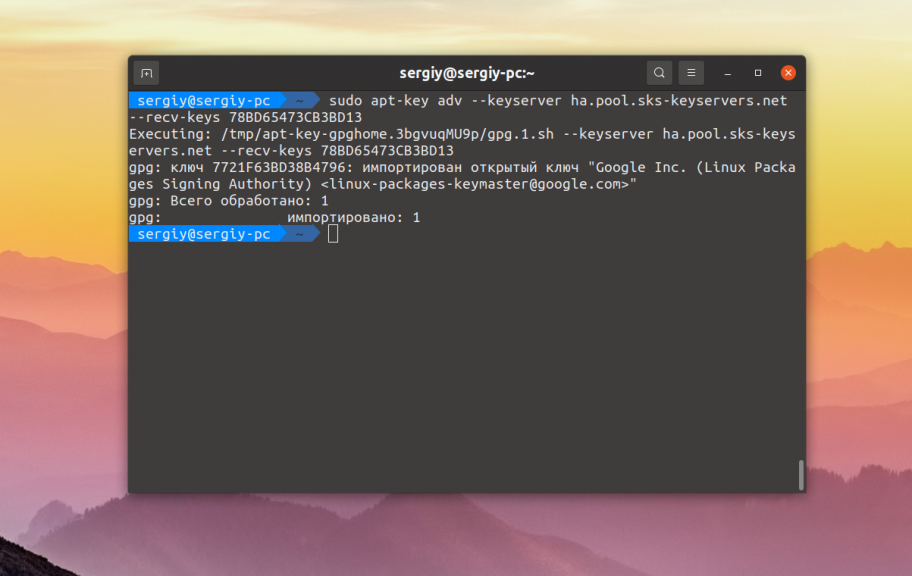
В данном случае не хватает ключа от репозитория Google — 78BD65473CB3BD13. Можно попытаться получить его с серверов Ubuntu:
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 78BD65473CB3BD13
Или с другого сервера:
sudo apt-key adv --keyserver ha.pool.sks-keyservers.net --recv-keys 78BD65473CB3BD13
Если у вас нет ключа от PPA или любого другого репозитория, связанного с разработчиками Ubuntu это должно помочь. Ну и ключ от репозитория Google там есть:
Если же вы получаете ошибку. Ищите данный ключ в интернете, если ключа нет на сайте разработчика, то его можно найти на различных форумах. Скачайте его и добавьте в систему такой командой:
sudo apt-key add /путь/к/файлу.gpg
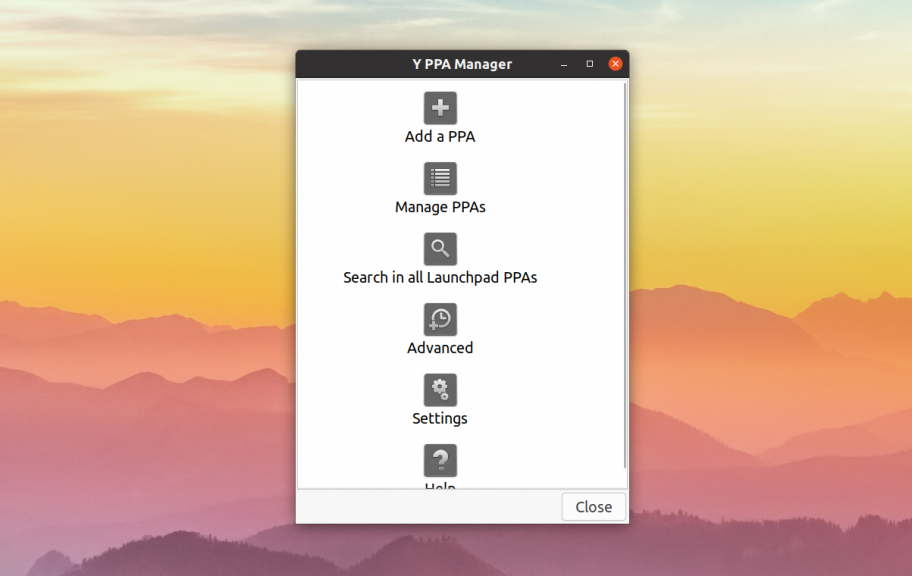
Ещё одна альтернатива первому способу — попытаться использовать графическую утилиту Y-PPA-Manager от webupd8. Для её установки выполните такие команды:
sudo add-apt-repository ppa:webupd8team/y-ppa-manager
sudo apt install y-ppa-manager
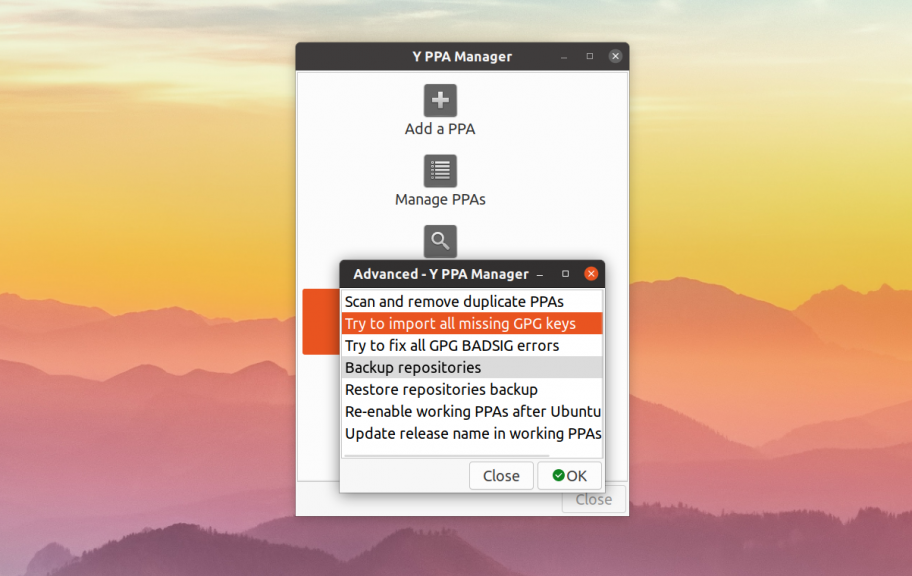
Затем запустите программу из главного меню или терминала. В главном окне программы выберите Advanced:
В открывшемся окне выберите Try to import all missing GPG keys, а потом дождитесь завершения работы утилиты:
После того как ключ добавлен вы можете снова попытаться импортировать репозитории и на этот раз у вас должно всё получится.
Выводы
В этой небольшой статье мы рассмотрели что делать когда возникает ошибка gpg недоступен открытый ключ и как исправить эту ошибку. Даже не думайте, что что можно обойтись без ключа. Все методы, которые позволяли просить APT игнорировать проверку ключей в современных версиях дистрибутива уже не работают. Если у вас остались вопросы, спрашивайте в комментариях!
Статья распространяется под лицензией Creative Commons ShareAlike 4.0 при копировании материала ссылка на источник обязательна .
Об авторе
Основатель и администратор сайта losst.ru, увлекаюсь открытым программным обеспечением и операционной системой Linux. В качестве основной ОС сейчас использую Ubuntu. Кроме Linux, интересуюсь всем, что связано с информационными технологиями и современной наукой.
Опубликовано 21.12.2021
При установке пакетов в Debian или Ubuntu, при выполнении команды apt-get update иногда возникает ошибка W: GPG error: [..] Release: The following signatures couldn’t be verified because the public key is not available: NO_PUBKEY [..].Обычно проблема возникает после добавления нового репозитория в /etc/apt/sources.list.
W: GPG error: http://apt.server.local buster InRelease: The following signatures couldn’t be verified because the public key is not available: NO_PUBKEY GDF123EF1FCB234E
E: The repository ‘http://apt.server.local buster InRelease’ is not signed.
N: Updating from such a repository can’t be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration detail
Причина возникновения: Отсутствие GnuPG-ключа репозитория.
Хеш ключа указывается в указывается в тексте ошибки после NO_PUBKEY. В данном случае, из примера выше GDF123EF1FCB234E.
Установка GPG ключа в систему
gpg --keyserver keyserver.ubuntu.com --recv KEY
gpg --export --armor KEY | sudo apt-key add -Пример:
gpg --keyserver keyserver.ubuntu.com --recv GDF123EF1FCB234E
gpg --export --armor GDF123EF1FCB234E | sudo apt-key add -Более просто вариант:
apt-key adv --recv-keys --keyserver keyserver.ubuntu.com KEYПример:
apt-key adv --recv-keys --keyserver keyserver.ubuntu.com GDF123EF1FCB234E